What is network sniffing? Information is sent across networks in groups called packets. Network sniffers then intercept these packets in order to find information about a network.
Chess, the Force, and Duct tape all have a dark side and a light side. Network sniffing is no different and can be used in both ethical and illegal ways. Developers often check the network in order to confirm the information they are sending is being received accurately and that there aren’t any problems. If there are, examining the network can help with troubleshooting and fixing. Illegal usage can span from simple information gathering to pretending to be a valid site or service to masquerading as a user.
Man in the Middle Attack
When a hacker poses as a service agency, it is called a man in the middle attack. The hacker acts as both the agency and victim, thus tricking each into thinking they are talking with the other. Using this technique allows the man in the middle to access any information sent to or from a computer in the network. This is a passive attack used for information gathering.
Sidejacking
Hackers don’t need raw data like usernames and passwords to do damage. Many websites send your computer a cookie. Cookies are packets of information that let the site know you are familiar and store useful information like pages visited. These cookies allow you to resume where you left off and avoid logging in every visit. With sidejacking a hacker takes cookies that were transmitted over an unsecure network. Then they can access accounts as if they are the user.
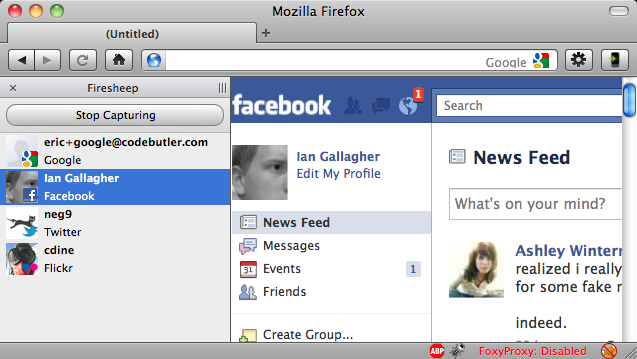
Image by {codebutler}
To raise awareness and demonstrate the vulnerabilities that sidejacking exploits, a developer created a Firefox extension in 2010 called Firesheep. This program made it easy for anyone, regardless of development knowledge, to experience the power websites give hackers when they don’t use SSL.
Local Area Network Attacks
Wireless
There are a couple of ways this is done depending on the network environment. When information is sent across a Wireless Local Area Network (LAN), every computer in the network has access to the information packets as they travel. Think of it like a noisy restaurant. Just like you ignore talk not directed at you, most computers are configured to just ignore any packets that are not addressed to them. A user only has to make the computer accept all packets for this type of network sniffing.
Wired Network Attacks
Wired networks are much more difficult to infiltrate. Because computers send information directly to the router, packets aren’t exposed to everyone on the network. In order to collect the information travelling on this system, a user would need to physically plug into it. Since the router is the location where information flows, they would need direct access to it to install a packet analyzer. This is primarily used by system admins to monitor traffic and troubleshoot.
Keep Your Information Safe
Monitoring traffic using network sniffing can catch problems before they get out of hand. In one company’s case, it could have alerted them that one of their employees had outsourced his work to China. While it seems like a genius move on the part of the employee, the potential damage to the company he worked for is substantial. NDAs could be broken, sensitive information leaked, buggy code written, or backdoors added to projects. If they had kept an eye on their VPN traffic, the employee wouldn’t have been able to continue scamming the company for months.

SSL
Now that you are aware of the vulnerabilities of using a network, you may be wondering how to protect your information. The simplest way is to use a secure sockets layer (SSL). Many websites have defaulted to this new protocol to protect their users and Google rankings. You will know if the website supports SSL by using https instead of http in the url.
VPN
Another option for accessing a network securely is to use a Virtual Private Network (VPN). VPNs are exactly what their name describes, a way to access a private network virtually. Since you are not using John Doe’s insecure wireless network, your information flows exactly where you want it, without the possibility of compromised computers leering at it. Another benefit to business VPNs is the ability for employees to remotely access information and tools remotely that are stored locally.
Now What?
Network sniffing is a simple way for both hackers to steal information as well as for companies to monitor for illicit activity. Knowing about these capabilities and the types of attacks that can be executed is the first step in protecting yourself and your company. Check out our other security blogs for more ways to stay secure and learn how Metova and CyberCENTS are keeping both our customers and America secure.