As technology in security improves, so do hackers’ proficiency in hacking. Getting started with minimizing security risks and protecting your company doesn’t have to require a huge chunk of your budget or an in-house expert. Here are 5 simple ways you can start protecting your business today.
Screen Locks
Ever heard of the phrase “the walls have ears”? Well, in the case of computers, email, and chat, the walls also have eyes. One of the easiest things to do to safeguard your IP is to be protective of who can view your computer screen. It is easy to become very complacent about this if you work from home or in an office where your coworkers are all on the same project and knowledge is shared freely. If you ever have clients visit the office or take your work with you to a coffee shop, turning these next tips into habits will help keep your work more secure.
When in a public place, examine the layout. Find a secluded area facing the room with your back to the wall. This will minimize the number of people who could see your work as well as keep strangers from looking over your shoulder. If you get up to leave your computer for any reason, even “just one minute”, use a screen lock and password. It is easy to get distracted and one minute can quickly turn into several.
How to set up screen locks on Windows.
How to set up screen locks on Macs.
VPN
Another security risk that occurs when you are using your computer away from your home or work is from public wifi. If the connection is unsecure, the information you type into your computer as well as data about your online activity could be at risk for being stolen or abused. It’s also possible that instead of being connected directly to a service, your data is first being filtered through a hacker’s network. This is called a man-in-the-middle attack. A third, even more dangerous possibility, is that your computer becomes infected with malware. When this happens, hackers have more access to the information on your device, even when you are no longer using public wifi.
There a few steps you can take to protect yourself. Try to limit your use of public wifi and check that the network you are using is the one set up by whatever establishment you are in and not a fake one created by a hacker. When browsing the internet, visit websites that use OpenSSL. These are the ones with https:// in the url.
By far the best option is to implement a virtual private network, or VPN. This allows your computer to create a secure connection with a network of verified computers. It can also be set up so that you can securely access resources on your home or work network. If your business doesn’t already have a VPN set up, you can do it yourself. While there are some free VPN services, they are not recommended. Using these services just puts your data in someone else’s hands, which is the exact thing you are trying to avoid.
Multi-Factor Authentication
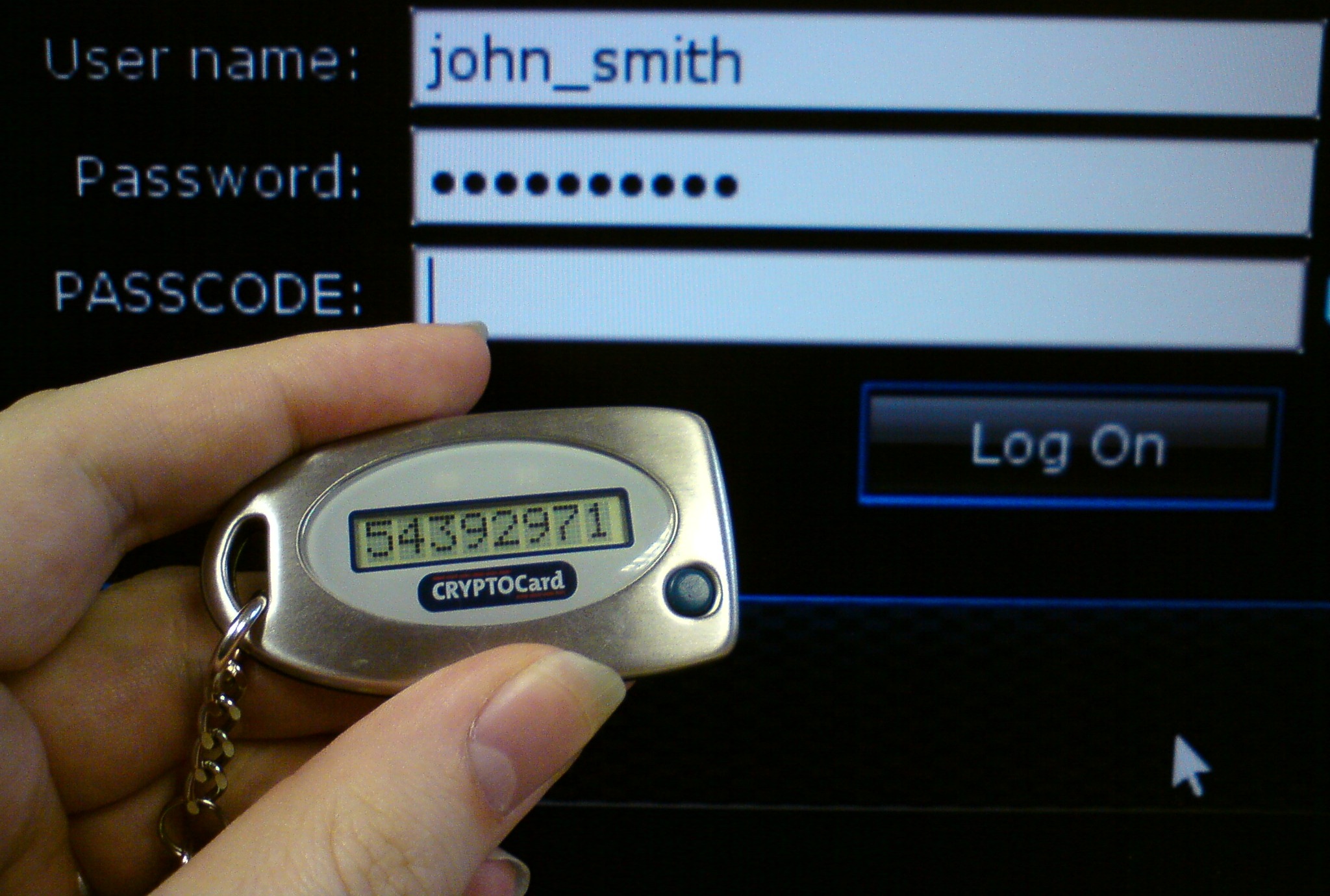
Image by By Brian Ronald, GFDL image
Multi-factor authentication, or 2-factor authentication, has been around since the early 2000s. It confirms a user’s identification via two sources: something you have (a security token) and something you know (a password). Now it is commonly done by requiring users to submit a code that was sent to their phone or email. Because this extra layer of protection requires hackers to have more information to get into your account than before, many are repelled by the extra hoops they would need to jump through. Amazon, Google, Twitter, Facebook, etc. all support multi-factor authentication in some form or fashion now.
Does it sound like a hassle? Try out Google Authenticator. Google Authenticator is a tool that makes the additional steps required to log in easier and less cumbersome, while still keeping everything secure.
Remote Wipe
No one plans to have their computer stolen or lost. It’s not just frustrating and costly to replace, a lost asset is a security risk. Luckily, there are ways to counteract this. At Metova, we register our Macs with iCloud and Find My Mac. Doing so allows us to lock down or wipe a device if the unexpected happens.
If you use Macs, add this to the checklist for new team member setup. It only takes a couple of minutes. You can access iCloud options from the System Preferences menu. Log in, ensure that the “Find My Mac” option is checked and you are good to go.
Locking or wiping your lost device can easily be done from the iCloud website. Then you simply enter your Apple ID, message that will be displayed on the lost device’s screen, and a passcode. When and if you do find your device, you can regain use of it by entering the code. Protecting your information using the options available in iCloud is so easy, it would be reckless to not do so.
Lookout

Technology has allowed business to become more mobile than ever before. Work doesn’t have to be done in the office. Smartphones allow for email, meetings, and text to happen at your fingertips almost anywhere. While the technology has been particularly great for the nomadic worker or workaholic, it has also caused smartphones to become another portal from which hackers can gather information.
Keeping your device secure is Lookout’s goal. They have been working on mobile security since before the first Android phone was released in 2008. Lookout helps keep your information secure through a predictive cloud powered by millions of sensors throughout the world. This predictive cloud looks for patterns to detect risk in ways that could be missed by other companies that rely on human analysis. Lookout is our mobile security partner, who we trust with securing our applications and recommend to anyone looking to secure their personal device or enterprise.
There will always be people looking for an easy win. Hopefully by using these tips, you and your business can avoid becoming an easy target.
Does your development project need to be secure?



